
In January 2018, NHS, the largest healthcare provider in the UK, had taken an important step to offshore patient data to the cloud. Of course, some NHS organizations had already made this move, but now this initiative is supported officially. Although this decision was made to gain a huge range of benefits that include greater data security protection and reduced running costs, a lot of cloud sceptics doubt if it was a wise choice.
Cloud security is now more dependent on the ability of business users to handle sensitive data, rather than on security services offered by cloud providers. In 2015, Gartner (News - Alert) predicted that customers will be responsible for 95% of security failures in the cloud through 2020. Netwrix 2018 Cloud Security Report supports this statement, as employee misbehavior was the main root cause in 58% of security breaches in 2017.
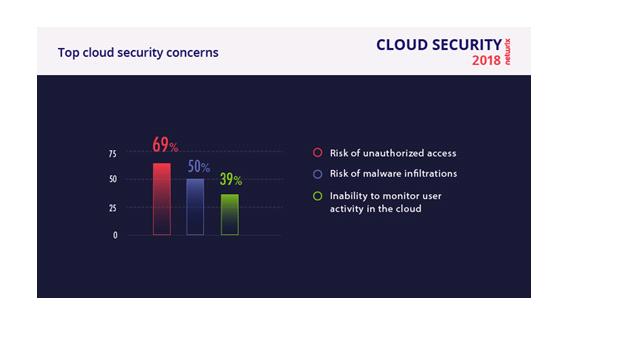
The results of the report revealed that cloud started to play a core part in business, but security is still an issue for the majority of respondents. In fact, 88% of IT pros believe that a cloud data breach can seriously impact their business. The same as last year, the top cloud concerns include risks of unauthorized data access (69%) and malware infiltrations (50%). The third most disturbing trend is that 39% of companies cannot monitor employee activity in the cloud, which replaced DDOS attacks that were popular in 2016.
Insiders have always been an issue for businesses, but in 2017 this problem exploded. Insiders were blamed by almost 58% of organizations for security incidents in the cloud. Although the majority of security attacks were external, in most cases insiders served as catalyst for the process. The vivid example is ransomware that is hidden in a phishing email. You just open a malicious attachment or click the link and voila, your organization is paralyzed by encrypting virus.
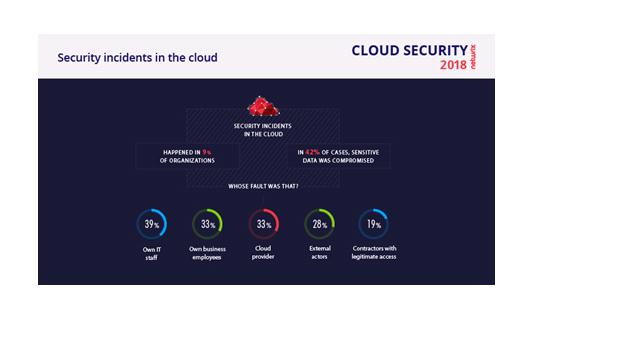
The fun fact is that although most companies understand insider threat, the majority of them still prefer not to dive into the problem and blame their own IT staff for security incidents in the cloud. What is more interesting, most companies don’t even try to find out a reason for an incident, as only 28% of organizations have visibility into what their IT personnel is doing, and even less can track activity of their business users, contractors and cloud providers.

Unfortunately, rich set of security controls offered by cloud providers (for instance, AWS offers 1,800 to choose from) is balanced by human factor and lack of visibility into user behavior. This is the main reason why the number of those who think that cloud had a positive impact has decreased since 2016 from 41% to 32%, and the number of those who named negative impact has increased from 11% to 27%.

However, cloud is a promising technology, which makes companies to rethink their approach and change the workflows. Security strategy that worked on premises is not applicable in the cloud. This makes IT departments to request extra budget and hire highly skilled professionals to drive security initiatives. The bad news is that only 66% of our respondents have support of the top management to achieve their goals.
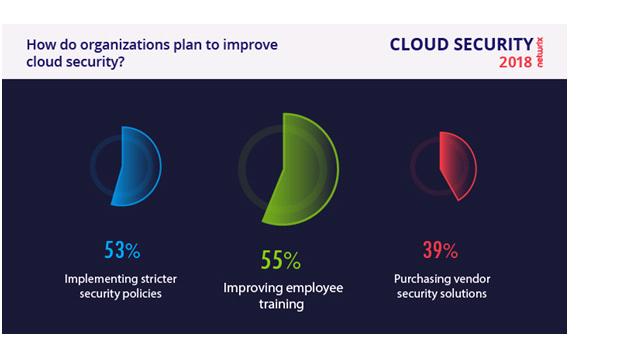
Management support is great, but usually it is stated only on paper. In practice, most companies have to settle for less and start with low-cost measures. Yes, human factor cannot be eliminated completely, but it doesn’t mean that we should stop trying. Teaching people what is good and what is bad is a thorny path, but still 55% of companies have chosen regular employee trainings as a way to improve at least cyber security awareness. The best advice here is to make the content entertaining, focus on current trends, add vivid examples and explain common traps used to fool a user as simple as possible.
Hardly any security training can go without toughening existing security policies. This measure was chosen by 53% of companies. Although this step is also very low-cost, it is very important and often underestimated. Everyone has their own vision of how to handle sensitive data, unless the exact security rules are documented. Make sure you adjust the policy to the existing threat landscape and update your colleagues about any changes.
Other steps include adding security layers with additional security automation software (39%) or developing in-house solutions (36%). Some companies (17%) include hiring more security professionals as a key initiative for 2018. Finally, 16% of companies are satisfied with the state of things and are not going to change anything. Meanwhile a fraction of respondents are going to move their data back on premises, as they turned out to be unprepared for the challenges of cloud adoption.
View the full 2018 Cloud Security Risks infographics:
https://blog.netwrix.com/wp-content/uploads/2018/01/Infographics_2018.jpg
Edited by Mandi Nowitz




